Recently I needed to setup URL filtering on Lync Server for a project. Pretty simple task you’d think, but I needed to exclude local intranet hyperlinks from being blocked as well. I found out that this is much easier said than done in Lync.
The Problem
Everything exists in the Lync Server Control Panel for this, and there is advice here on TechNet to configure it, but it’s very vague and only scratches the surface as to what is actually required. To get this working, you need to add the URLs you want to exclude to the Local Intranet Sites zone on each Front End Server, as per TechNet.
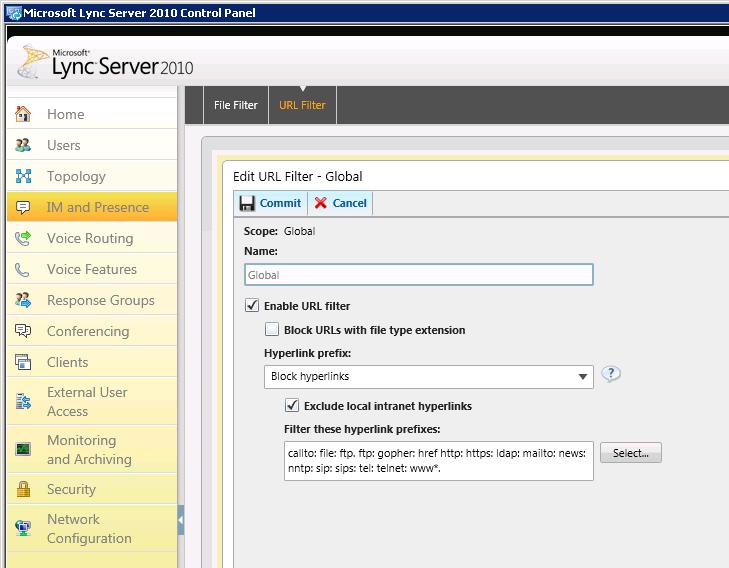
The URL Filter page in the Lync Server 2010 Control Panel
Sounds easy enough right? Wrong. Because the Lync Front End Server service now runs under the Network Service account, you can’t just open up your Internet Options and pop them in there, you need to open Internet Options as the Network Service account.
Usually to execute an application under a different account, you can use the runas command, which would look like this:
runas /user:”NT Authority\Network Service” “C:\Program Files\Internet Explorer\iexplore.exe”
This doesn’t work properly though, because you’re prompted for the Network Service password, which we don’t know (because this is a system account). The way around this then, is using the PsExec tool from SysInternals. The process to point you in the right direction for doing this is detailed here by Ben Parker (hat tip to Paul Nearney, a fellow Modality rockstar for bring this to my attention).
So using PsExec, the command we want to run is:
psexec -i -u “NT Authority\Network Service” “C:\Program Files\Internet Explorer\iexplore.exe”
This then fires up Internet Explorer for us, but we’re greeted with this when we open Internet Options:
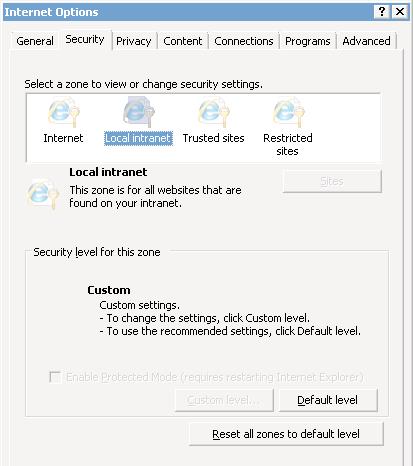
The Internet Options dialog when executed under the Network Service account
Pretty useless really, because we can’t change anything! We can’t click on Sites to add the URLs we want to exclude, so we’re stuck. This is where I escalated this problem to Microsoft.
The Workaround
I engaged Microsoft PSS and after some investigation and reproduction of the issue, the engineer (thanks to Debasis Mishra) and the Lync Product Group identified this as a bug and came back with a workaround.
To get this working today, we need to do a bit of registry hacking to add local intranet URLs manually to the Local Intranet zone:
The Network Service like all AD objects has a SID and that is unique and common across all. The SID of Network Service account is S-1-5-20.
- Launch the registry on the Lync Front End server and browse to HKEY_USERS\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains (in case you don’t find ZoneMap and Domains, create new keys with these names in the Internet Settings key).
- From here, we can add the first Intranet site which is, let’s say for example http://contoso.com.
- Under Domains, create a new key and name it contoso.com.
- Next, create a DWORD with name http and set the value to 1. You can do the same for https if you need this.
- Similarly for a second site, create a key and name it contoso.local for example.
- Here you need to create DWORD(s) for each protocol you want to allow. Let’s say one with the name https and the other with the name ftp. Set the value to 1 for both.
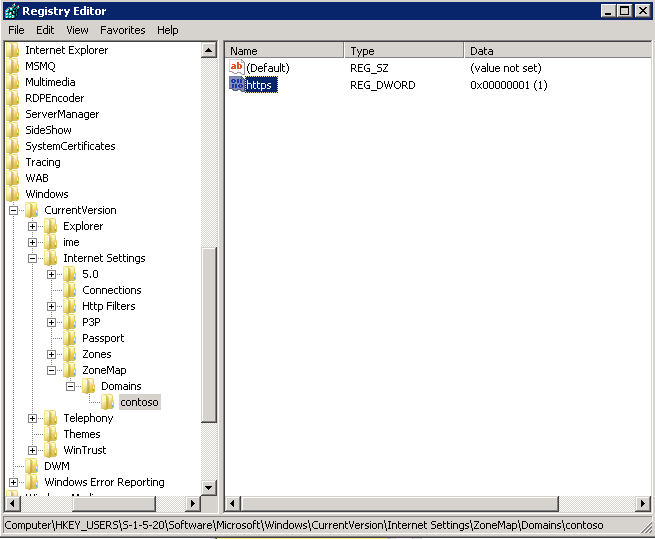
Excluding local intranet URLs from filtering in the Windows registry
- Once done, restart the FE service and you should now be able to send IMs with the intranet URLs you’ve specified e.g. http://www.contoso.com
And there you have it, that’s how you do it my friends. A bit convoluted right now and messy, but it get’s the job done. Hopefully a hotfix will be released in an upcoming Cumulative Update and the documentation will be updated.
Let me know if you have any problems with it in the comments section below.